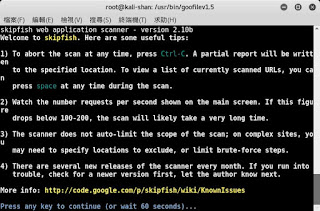
wpscan 說明
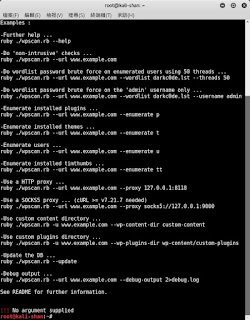
這是針對 wordpress偵測 wpscan _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 2.9.1 Sponsored by Sucuri - https://sucuri.net @ _ WPScan _ , @ethicalhack3r, @erwan_lr, pvdl, @ _ FireFart _ _______________________________________________________________ Examples : -Further help ... ruby ./wpscan.rb --help -Do 'non-intrusive' checks ... ruby ./wpscan.rb --url www.example.com -Do wordlist password brute force on enumerated users using 50 threads ... ruby ./wpscan.rb --url www.example.com --wordlist darkc0de.lst --threads 50 -Do wordl