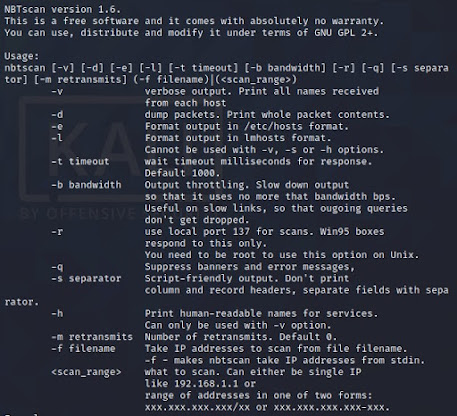
fimap說明
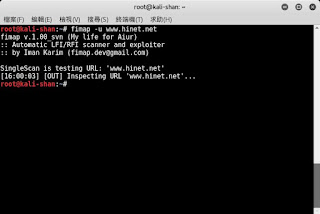
此是一種收集網址(IP)資訊,並攻擊的指令 針對LFI/RFI(local File Inclusion/Remote File Inclusion)特性去掃描跟攻擊 可叁考: https://www.youtube.com/watch?v=ODMHucZNQ9k ============================ 看看 help fimap -h fimap v.1.00_svn (My life for Aiur) :: Automatic LFI/RFI scanner and exploiter :: by Iman Karim (fimap.dev@gmail.com) Usage: ./fimap.py [options] ## Operating Modes: -s , --single Mode to scan a single URL for FI errors. Needs URL (-u). This mode is the default. -m , --mass Mode for mass scanning. Will check every URL from a given list (-l) for FI errors. -g , --google Mode to use Google to aquire URLs. Needs a query (-q) as google search query. -B , --bing Use bing to get URLs. Needs a query (-q) as bing search query. Also needs a Bing APIKey (--bingkey)